HARDWARE SECURITY COUNTERMEASURE
Anti-Counterfeiting Digital IP
 WHAT ABOUT IC COUNTERFEITING? Counterfeit Information and Communication Technology (ICT) goods accounted for 6.5 % of ICT global market in 2013, representing USD 143 bn of loss for the whole related industry (source: OECD). In addition to this illegal trade, a growing number of third-parties design and sale off-brand/compatible/generic electronic products, that are legal copies of the genuine electronic devices. Among all electronic systems available on the market, some are particularly targeted by copycats, such as printer cartridges, video game controllers & PayTV Control Access Systems. The use of the copied version of these devices in place of the genuine ones results in huge market share loss for manufacturers. On another hand, considering copy issues, when it comes to electronic-based systems and documents such as Passports, ID cards, Driving Licences, Smart meters or IoT, this is personal, governmental and industrial data confidentiality that are at risk.
WHAT ABOUT IC COUNTERFEITING? Counterfeit Information and Communication Technology (ICT) goods accounted for 6.5 % of ICT global market in 2013, representing USD 143 bn of loss for the whole related industry (source: OECD). In addition to this illegal trade, a growing number of third-parties design and sale off-brand/compatible/generic electronic products, that are legal copies of the genuine electronic devices. Among all electronic systems available on the market, some are particularly targeted by copycats, such as printer cartridges, video game controllers & PayTV Control Access Systems. The use of the copied version of these devices in place of the genuine ones results in huge market share loss for manufacturers. On another hand, considering copy issues, when it comes to electronic-based systems and documents such as Passports, ID cards, Driving Licences, Smart meters or IoT, this is personal, governmental and industrial data confidentiality that are at risk.
 HOW CAN ICs BE COPIED? To make such copies of electronic devices, copycats need to perform invasive attacks on the genuine Integrated Circuit (IC). An invasive attack consists in reversing the hardware, with the goal to discover where and how to access the precise point(s) where it is possible to take control of the component and then siphon its embedded code. From that point, the attacker is able to copy the code into a new IC and compete with the copied manufacturer with a much cheaper solution. This demonstrates how a weakness in the hardware can open full access to the boot code as well as the user’s code and data. One can deduct then that industry and governments can protect their electronic devices from counterfeiting and copy by enhancing the security of the hardware.
HOW CAN ICs BE COPIED? To make such copies of electronic devices, copycats need to perform invasive attacks on the genuine Integrated Circuit (IC). An invasive attack consists in reversing the hardware, with the goal to discover where and how to access the precise point(s) where it is possible to take control of the component and then siphon its embedded code. From that point, the attacker is able to copy the code into a new IC and compete with the copied manufacturer with a much cheaper solution. This demonstrates how a weakness in the hardware can open full access to the boot code as well as the user’s code and data. One can deduct then that industry and governments can protect their electronic devices from counterfeiting and copy by enhancing the security of the hardware.
HOW CAN THE HARDWARE PROTECT THE SOFTWARE? To be effective, this hardware-based security must entirely rely on itself, meaning that is cannot involve the software, as this one can be compromised during an attack. Moreover, as nothing can prevent from reverse engineering an IC, hardware security must be built « by design ». This means that even by recovering all the secrets of the ICs architecture, extracting the code is impractical. Such a hardware concretely secures the software by making it inaccessible to the attacker. This way, the electronic device cannot be emulated, copied, cloned or counterfeited.
 A SOLUTION NOW EXISTS TO PROTECT ICs FROM THEIR CODE EXTRACTION During the last years, while exploring ICs and evaluating their level of resiliency against counterfeiting and copy, we discovered at Texplained that all of the components that we have looked at so far are vulnerable to code extraction. We also realized that no solution exists on the market to make the hardware more secure regarding invasive attacks and counterfeiting. Then, we decided to take advantage of our experience in real world attacks, our knowledge of ICs architecture and weaknesses and our competencies in digital design to imagine and design solutions that effectively protect ICs against embedded code extraction. As a result of this R&D investment, « NVM Defender » was born! We are now able to provide chip makers who want to protect their assets and those of their customers from the theft and copy with a truely hardware protective IP!
A SOLUTION NOW EXISTS TO PROTECT ICs FROM THEIR CODE EXTRACTION During the last years, while exploring ICs and evaluating their level of resiliency against counterfeiting and copy, we discovered at Texplained that all of the components that we have looked at so far are vulnerable to code extraction. We also realized that no solution exists on the market to make the hardware more secure regarding invasive attacks and counterfeiting. Then, we decided to take advantage of our experience in real world attacks, our knowledge of ICs architecture and weaknesses and our competencies in digital design to imagine and design solutions that effectively protect ICs against embedded code extraction. As a result of this R&D investment, « NVM Defender » was born! We are now able to provide chip makers who want to protect their assets and those of their customers from the theft and copy with a truely hardware protective IP!
WORLD’S FIRST DIGITAL IP PROTECTING CHIPS
FROM DATA EXTRACTION
NVM DEFENDER
Texplained’s first countermeasure protects the most essential part of a design:
Embedded Software, Cryptographic Keys and Personal Data
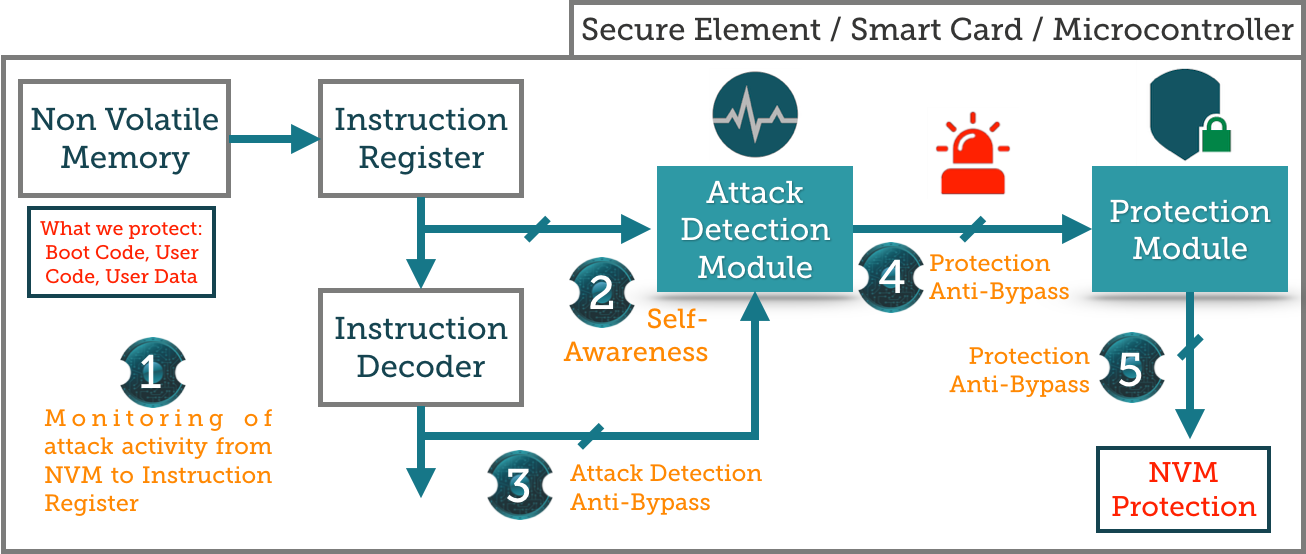
NVM Defender is the first hardware module which protects ICs from the most common invasive attack consisting in NVM Code extraction. Any IC integrating NVM Defender is protected against copy, emulation, cloning and counterfeiting. This pioneer solution is self-aware, meaning that the attack is detected on the fly. Moreover, the countermeasure structure in itself makes bypass impractical. Effective, Easy to Integrate and Cost-Effective, NVM Defender brings Security By Design to chip makers and integrators willing to protect their assets.

ANTI-COUNTERFEITING SOLUTION
Receive our NVM Defender Datasheet
A TRUSTABLE MODULE FOR A TRUSTABLE DEVICE
