HARDWARE SECURITY SERVICES & SOLUTIONS
IC Security Exploration & Protection
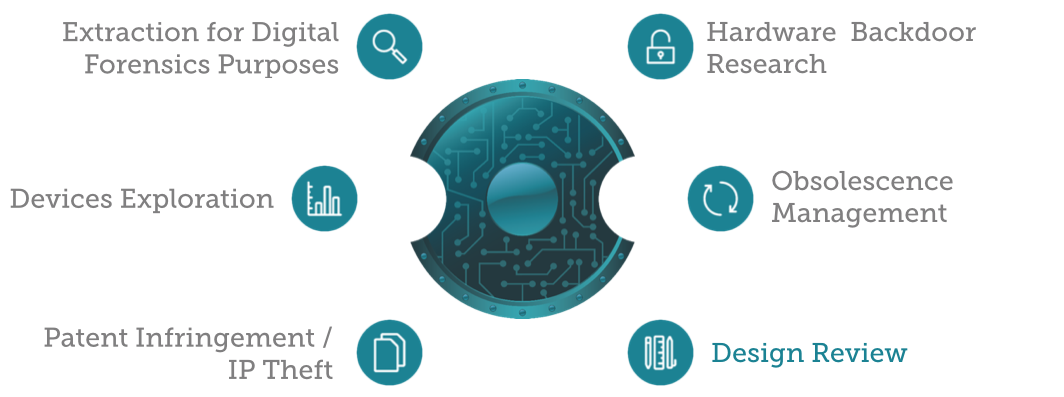
HARDWARE EXPLORATION SERVICES
COUNTERMEASURE
2 Main phases on hardware exploration for an A to Z chip analysis
PHASE 1: SAMPLE PREPARATION & IMAGERY In our lab, our equipments and expertise allow us to produce a wide range of images of ICs: from product shots and nice quality optical images to high resolution SEM pictures. => Optimal images of a chip are very useful for a first analysis of its architecture as it gives a first view on the different blocs composing the IC (memories, digital cores, analog parts, etc.). => “Chip ID” gives information on the physical construction of the device such as its number of layers, technology node and material (Copper / Aluminium) => Electronic images of the chip is the base material for a complete reverse engineering of the logic (phase 2)
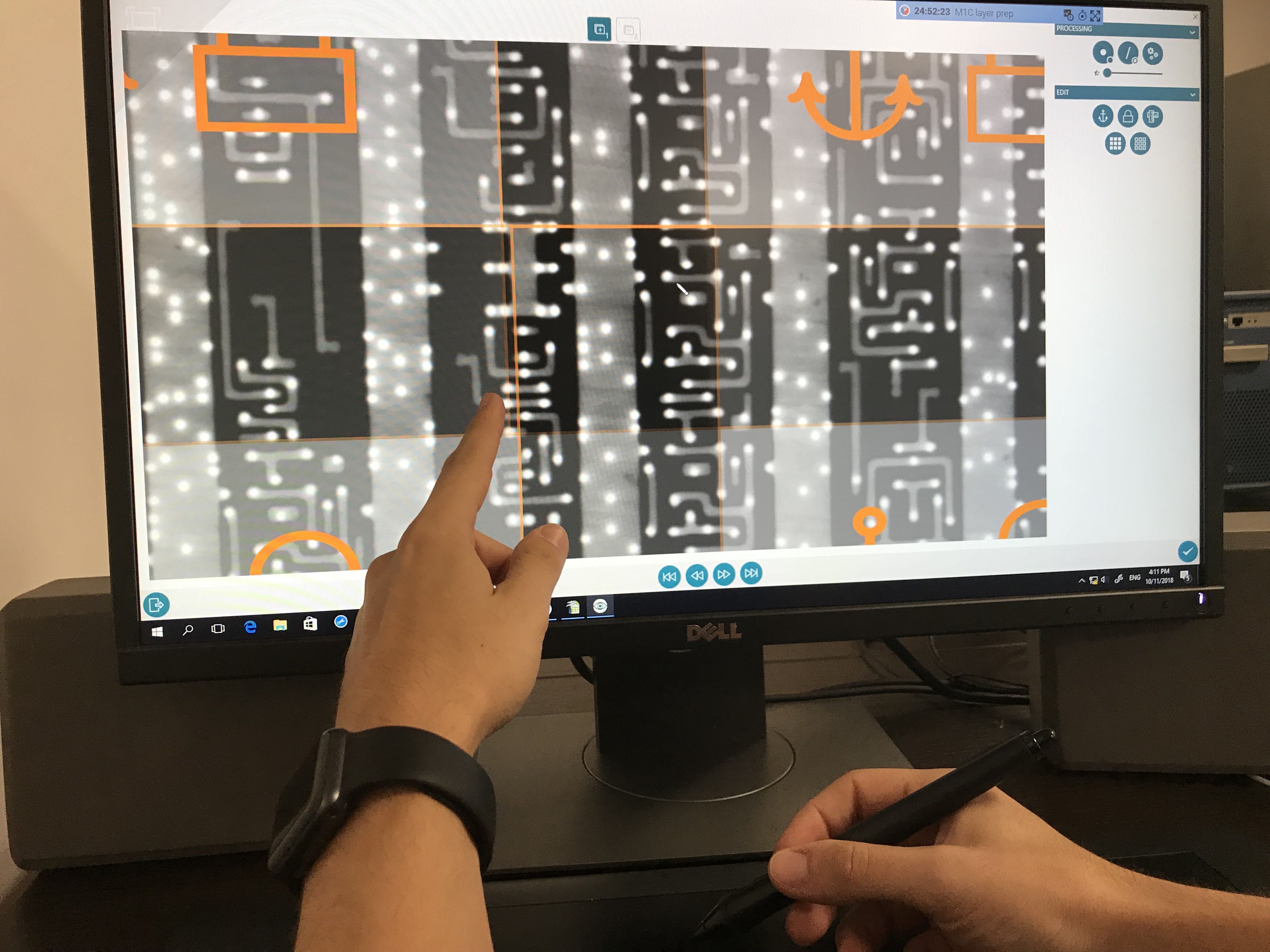
PHASE 2: IC REVERSE ENGINEERING Thanks to our cutting-edge proprietary tool ChipJuice we are able to perform efficient in-depth
exploration and then analyses of ICs. We are able to make many different kinds of studies on ICs architecture, implementation and
security, from « ID Card » and Standard Cell Library Reports to complete detailed reports. We assess the global threat to chip’s
security: non-, semi- and fully-invasive attacks are scanned thanks to our tools and experience. Find the details of our methodology for
ICs’ security evaluation here To be autonomous on your own hardware analyses you can access our online resources or order
specific images and then explore ICs by using ChipJuice, our in-house reverse engineering software.
More than 10 years experience on hardware reverse engineering & security
ChipJuice has been developed to operate fast and intuitively in-depth exploration of any kind of IC. From the electronic images of one chip internal, the tool recovers its whole architecture and delivers different formats of description such as Netlist, GDSII, Verilog files, etc. Our tool offers: => Intuitive workflow making netlist extraction easy and fast => The opportunity to look inside every type of IC whatever its architecture, complexity or size => Learning capabilities to make each new analysis faster by using the previous ones Indeed, ChipJuice allows the performance of complete black box studies Discover our Reverse Engineering Tool for ICs
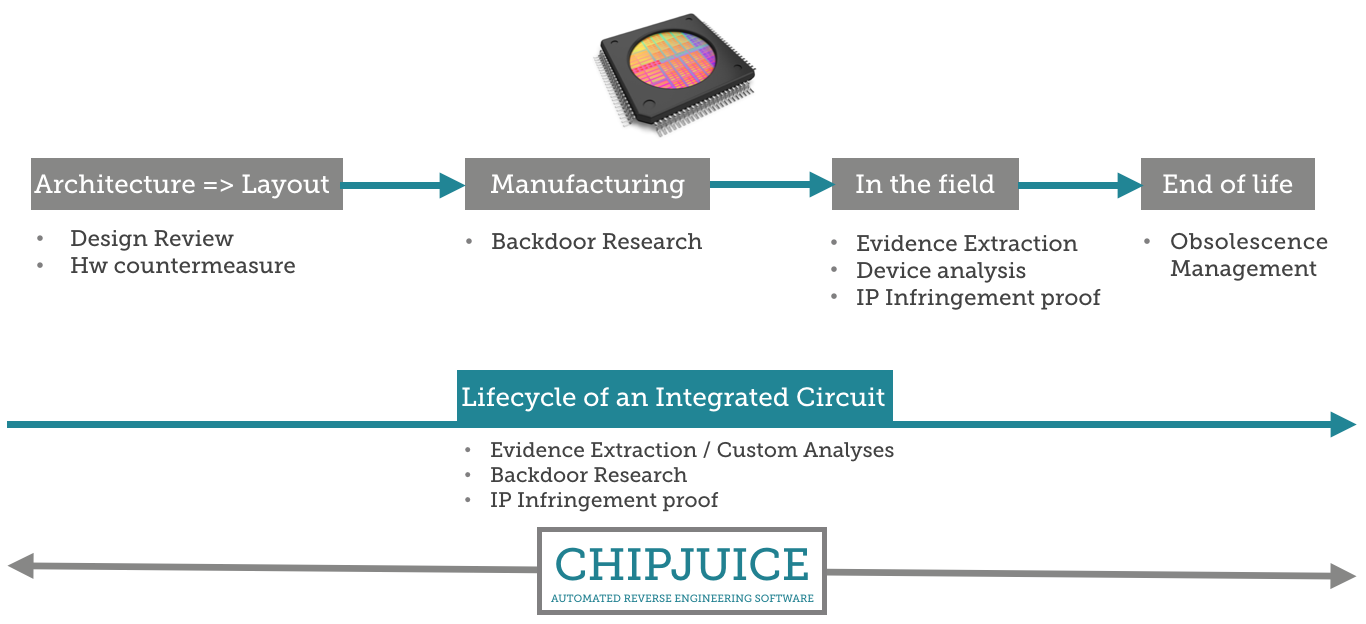
HARDWARE IN-DEPTH EXPLORATION A 360° approach for IC reverse engineering and security analysis ensures the best understanding and control of the hardware level of protection:
- We look at ICs’ security considering all types of hardware attacks
- We accompany you during the whole lifecycle of one’s chips or devices
Therefore, different services and solutions are offered to help and accompany you at every stage of the chip’s lifecycle: